
Beginners guide to Azure Bastion
Azure Bastion has had some changes since this post has been written. New post will be available in Nov/Dec and linked here.
What is Azure Bastion Service and how you can set it up and use it? And why should you? These are few thing that I’ll cover in this post. If you are not that eager to read you can check my presentation about the topic here.
When connecting to virtual machines that reside in Azure you need to have some kind of jump host or a bastion server to establish connection. Opening RDP connections over internet with public IP address is never a good idea. It is of course possible to use, for example, VPN to be able to connect your environment securely but that also needs bunch of configuration.
What is Azure Bastion?
Azure Bastion is a fully managed PaaS service that resides inside your virtual network. It can be deployed with just a few clicks after which you are able to establish RDP or SSH connections to your virtual machines securely over SSL without never needing to expose your virtual machines to e.g. public internet. All of this can be done in Azure Portal without any additional software, agents or clients. It is possible to have up to 50 concurrent SSH and 25 RDP connections.
Pricing for Azure Bastion is, according to Microsoft’s pricing page, 0,161€/hour. You’ll also pay for outbound traffic (5Gb/month is free). More information on pricing can be found here. I have found that when running in production environment cost are around 120€/month which can be seen to indicate that Azure Bastion is just running non-stop.
Let’s check how Azure Bastion is set up:
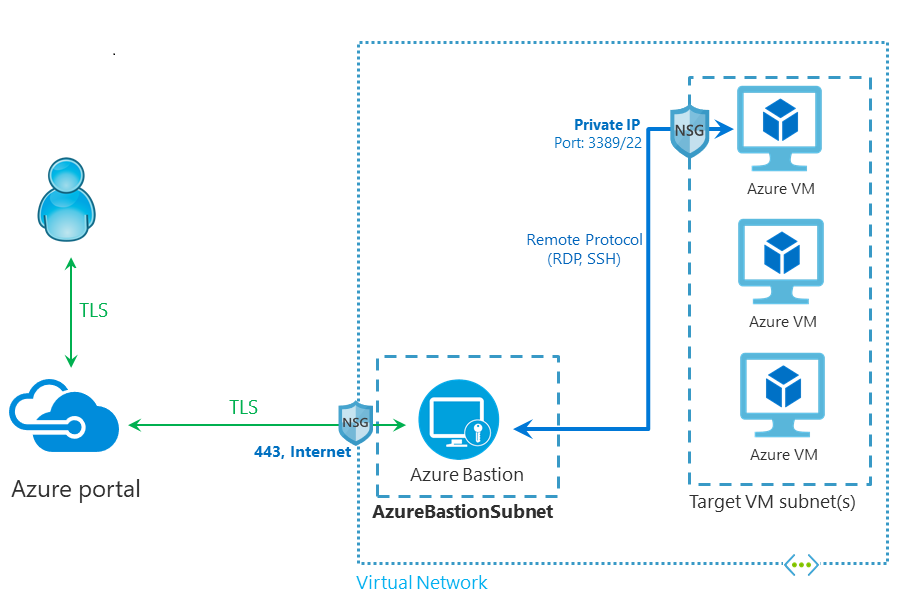
As we can see in the diagram RDP and SSH connections are only inside virtual network. User connects first to Azure Portal and from there connection goes to Azure Bastion over SSL/TLS which then establishes RDP or SSH connection to virtual machine itself.
One of the highly anticipated features arrived in the beginning of November when Azure Bastion VNet peering was announced to be in Public Review. This makes it possible to use one Azure Bastion to connect multiple virtual networks. Before it was needed to deploy one Bastion per virtual network and if you had bunch of those it could get pretty expensive pretty soon.
Deploying Azure Bastion into an existing VNet
Before it is possible to deploy Azure Bastion you need to have a Virtual networks in place. Virtual network in question needs to contain a subnet named AzureBastionSubnet which has a prefix of at least /27.
As always we start by navigating to Azure Portal and clicking ‘Create a resource’. Search for ‘bastion’ and start to create a bastion host.
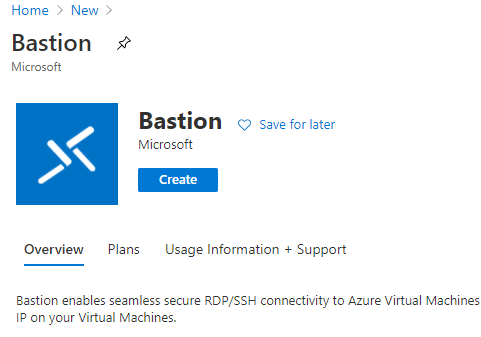
After clicking ‘Create’ fill in the necessary information. If you have AzureBastionSubnet created it pops up autotically when selecting Virtual network. You will also need to create Public IP address or if you already have one (as I did) just select that.
That’s basically everything that is needed. You can of course add tags if needed but otherwise Azure Bastion can now be created. Deployment takes few minutes.
Deploying Azure Bastion into a new VNet
Azure Bastion is possible to deploy at the same time during Virtual network deployment. In this case when you are creating a VNet you can simply select BastionHost on Security tab and fill in the necessary information. Note that here you need to have bastion subnet with a prefix of at least /26.
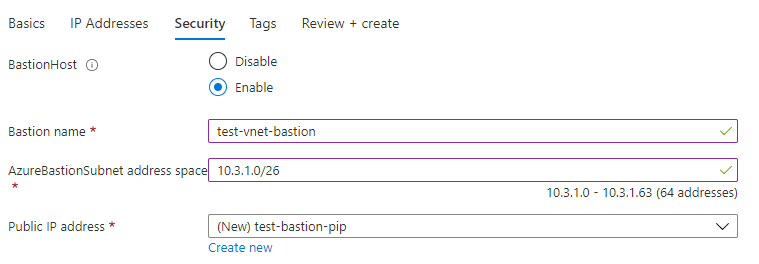
After filling all of the necessary information in the fields just click Review+create -> Create and new VNet with Azure Bastion is deployed.
Adding an NSG to AzureBastionSubnet
Even though it isn’t mandatory to attach Network Security Group (NSG) to AzureBastionSubnet it can can be a good idea to do so. When attaching NSG it should have certain inbound and outbound rules set in. If you don’t have rules needed NSG cannot be attached at all.
These are the inbound rules needed:
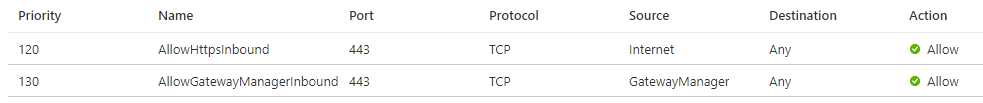
These are the outbound rules needed:
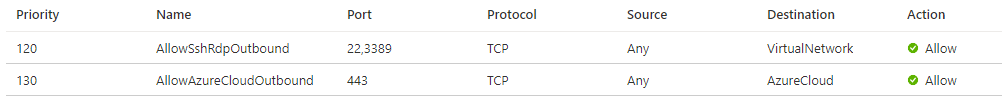
Enabling VNet peering for Azure Bastion
To enable VNet peering for you Azure Bastion only thing you need to do is to peer your VNets. If you have NSGs in place connections from AzureBastionSubnet needs to be allowed to target Virtual Machine’s VNet.
When peering is enabled you will be able to connect to Virtual Machine in an other VNet through bastion.
Connecting VMs using Azure Bastion
Users that are connecting Virtual machines through Azure Bastion will need to have following access rights:
- Reader role on the Virtual machine
- Reader role on the NIC attached to Virtual machine
- Reader role on the Azure Bastion
To connect VM through bastion you’ll need to navigate to VM blade, click ‘Connect’ and choose ‘Bastion’.
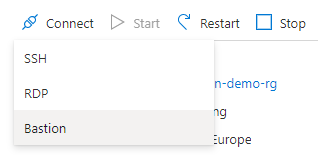
After this you still need to click on ‘Use Bastion’.
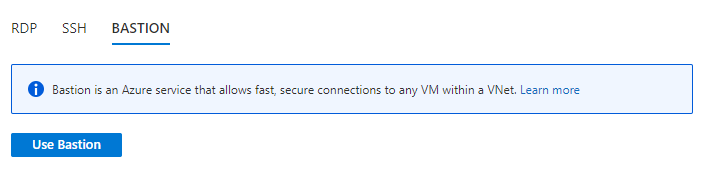
When connecting to Windows machines you can use username and password for the local machine or if Virtual machine is joined to domain you can use your domain account. In case of Linux machines you can either use username and password or SSH private key depending on your configuration.
Fill in your username and password and session will open into a new browser window/tab.
If you want to utilize copy-paste for text make sure to enable that when your browser asks for it.
User rights, notes, etc.
One thing to note is that if user has reader role for the whole Azure subscription he/she also has the ability access all of the Virtual Machines through Azure Bastion (only if he/she has credentials to actually log in to server though). If this is the case in your Azure environment some kind of custom role may be needed.
It is not possible to copy files from your computer to VM over Azure Bastion. If this is something that you need frequently then this solution might not be for you. Of course this can be handled for example by utilizing Azure storage and file share that is mapped to VM.
One thing that occasionally pops up at the bottom of my screen when connecting VMs through Azure Bastion is this message which in most cases seems to have no impact whatsoever but note that you may experience some instability and connection issues from time to time.
More information can be found following these links:
Azure Bastion documentation
Azure Bastion FAQ
Azure Bastion pricing